A Better Way To Manage Your Business Finances
Ditch the outdated methods—manage your business smarter with Kledo accounting software! Create invoices, track purchases, generate reports, and analyze your performance with ease. Practical, powerful, and accessible anytime, anywhere.
- Save 50% Administration Time
- Access 50+ Financial Reports
- Reduce Errors Up to 90%
Used by 75,000+ Companies and SMEs in Indonesia
Free Your Business from Financial Twists
Overcome manual recording, slow reporting, and complicated inventory management with Kledo, accounting software that automates financial processes instantly and accurately.
-
Process Automation
Save up to 50% of time with an automated system that processes invoices and financial transactions instantly, minimizing errors by up to 90%.
-
Real-Time Financial Reports
Access over 50 financial reports that are always up to date, allowing you to make quick and informed decisions based on accurate data.
-
Seamless Integration
Integrate your Kledo account with BCA Bank, Shopee, Tokopedia, Kledo Pos accounts, and payment gateway solutions such as Xendit and Midtrans.
-
Automatic Backup
Your financial data is automatically backed up to maintain integrity and ensure no important information is lost.
Maximize Your Gains with Smartly Tracked Chains
Try It Free Now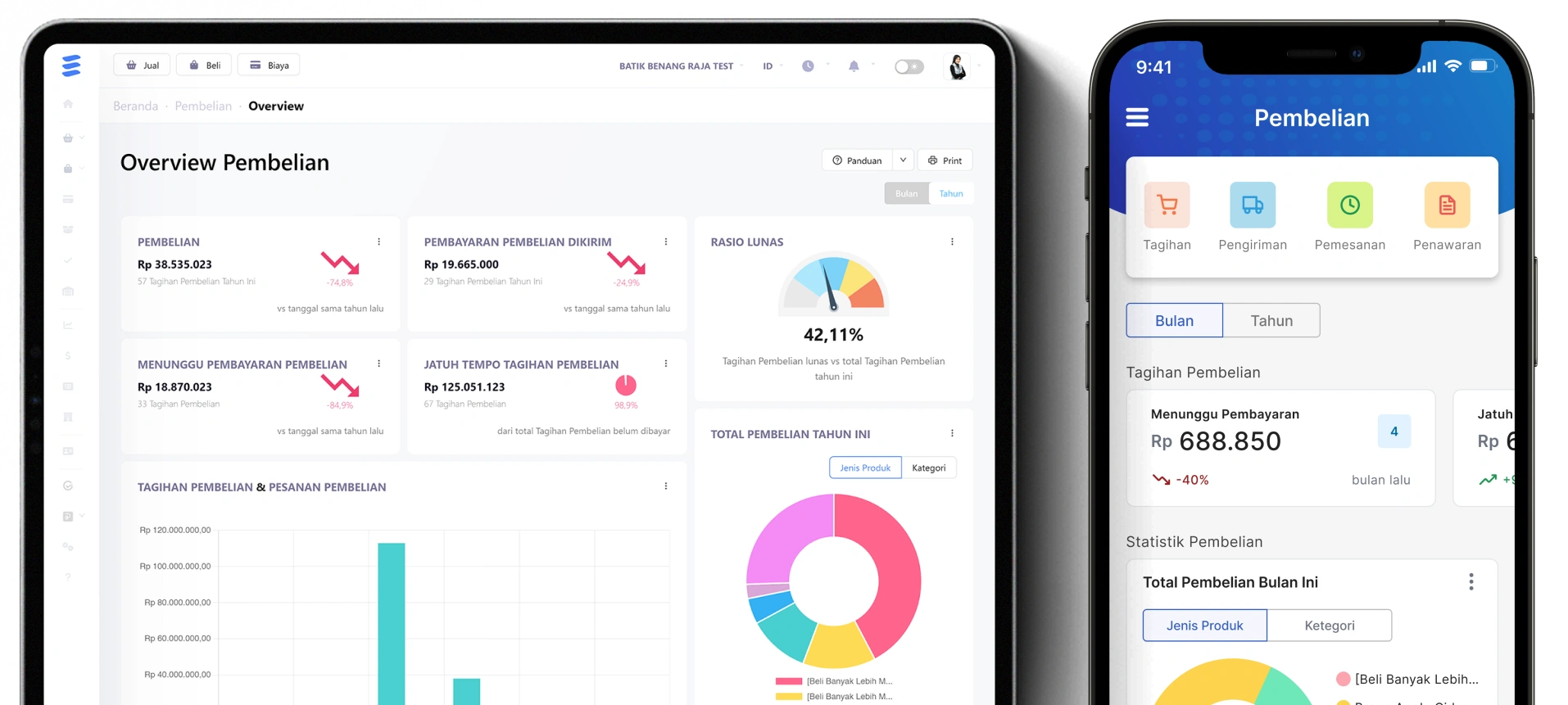
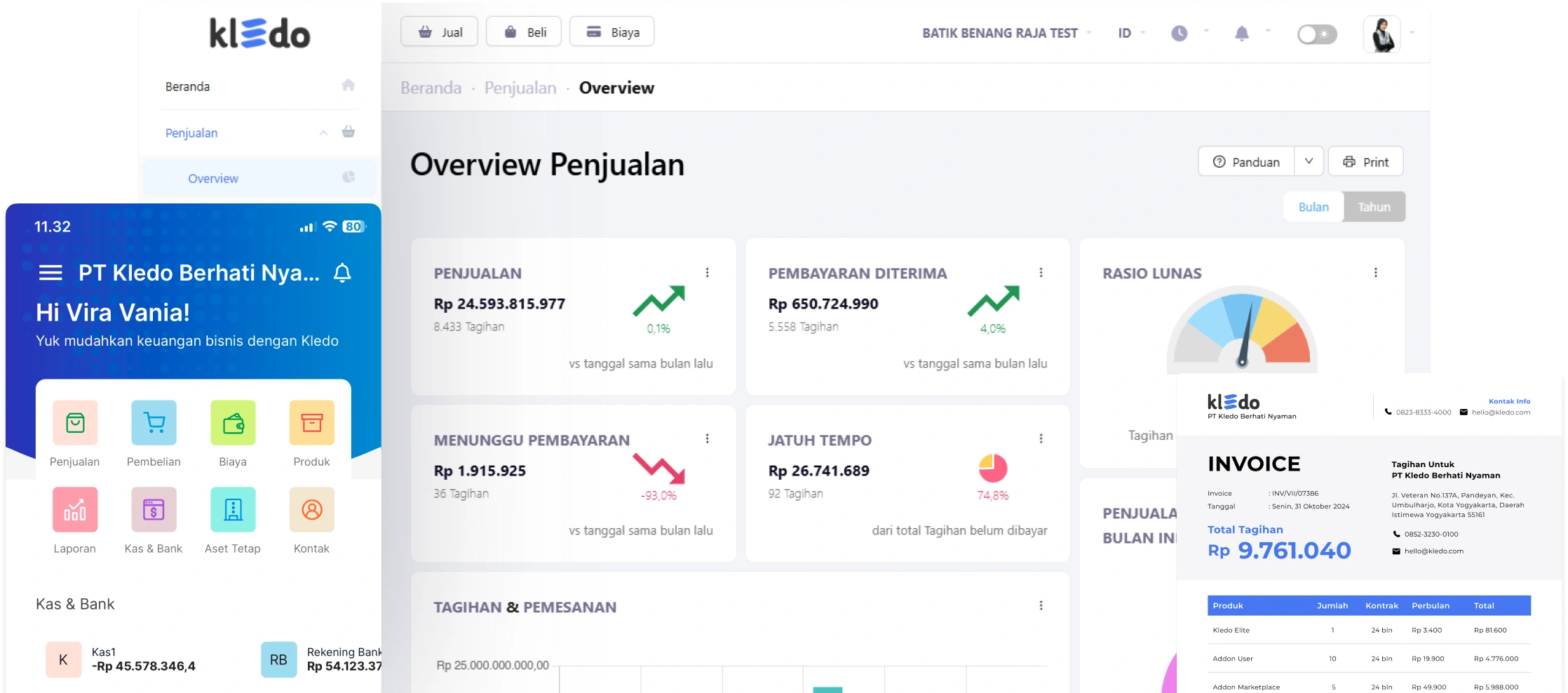
Leave the hassle of manual recording behind. Kledo presents real-time financial reports ranging from
transactions to inventory, all centralized in one easy platform.
Monitor cash flow, send invoices, and manage purchasing without hassle, so you can focus on developing
your business, not on administration.
Why Kledo is the Right Choice for Your Business
Cloud Based Accounting Software
No need to install and can be accessed from iOS, Android, Mac, Windows or any gadget.
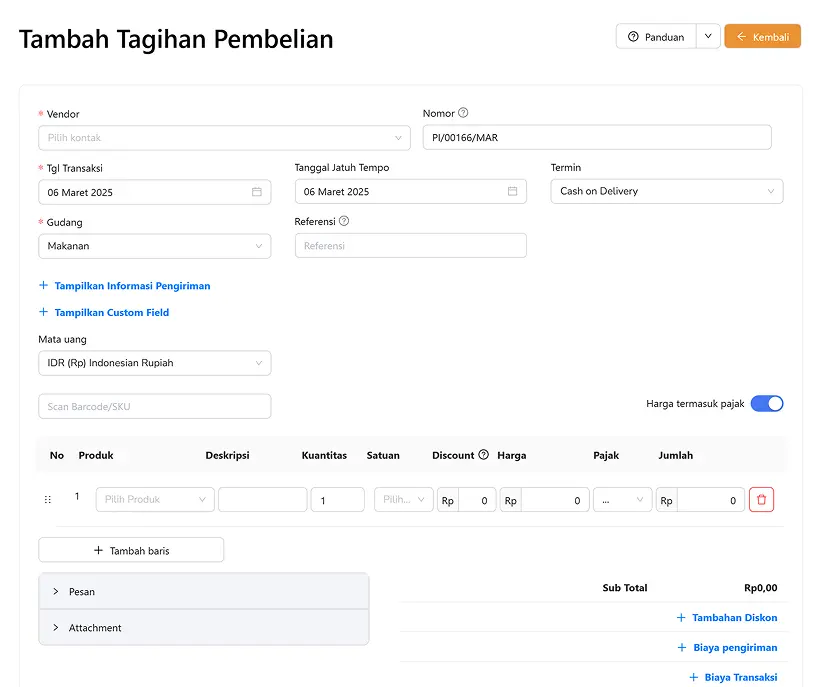
Purchasing
Create purchase orders and invoices in one easy step.
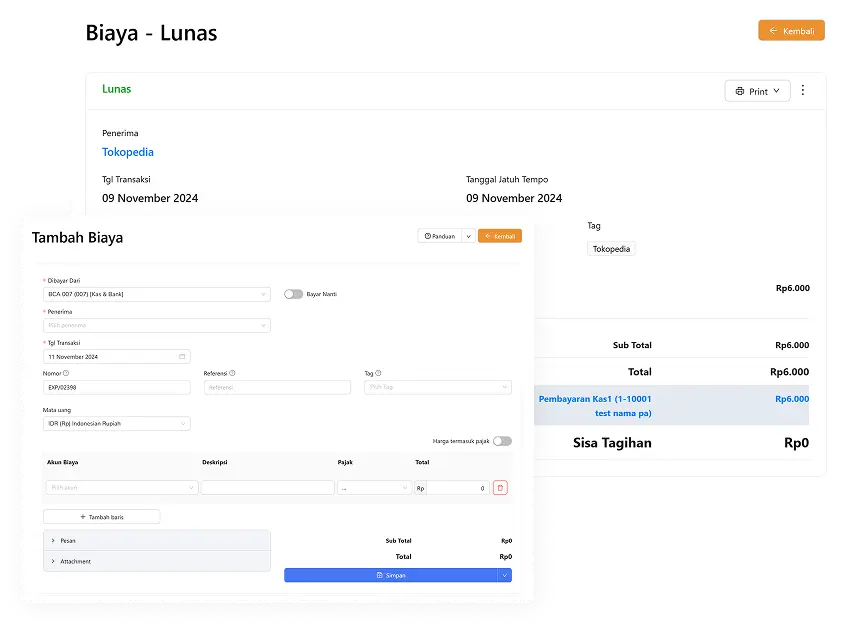
Cost Recording
Record expenses, track expense items and get detailed expense reports.
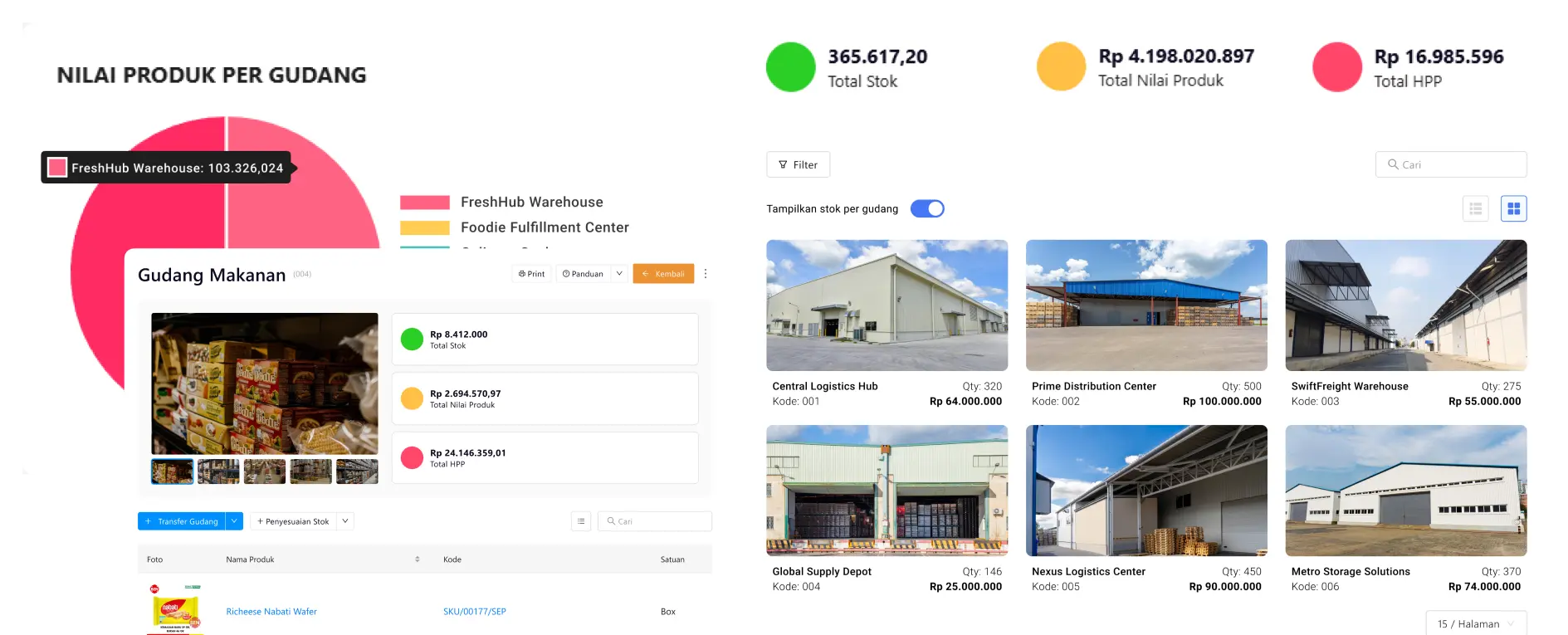
Stock & Inventory
Track product stock and inventory. Do stock opname. Can be multi-warehouse and multi-branch!
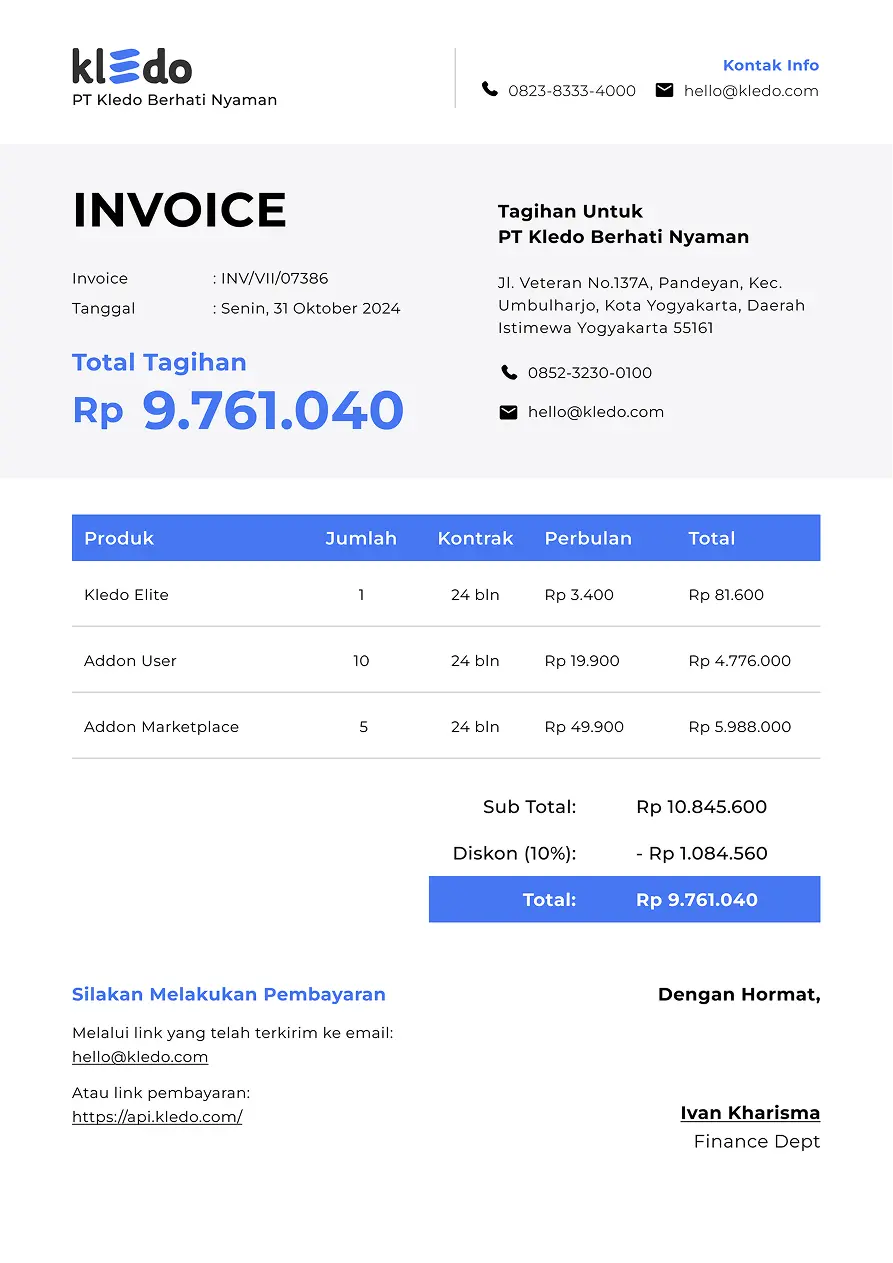
Invoicing
Leave the old way of creating invoices. Faster, more practical and get automatic reports!
Auto Fixed Assets
Track fixed assets efficiently, calculate depreciation automatically, and get real-time reports.
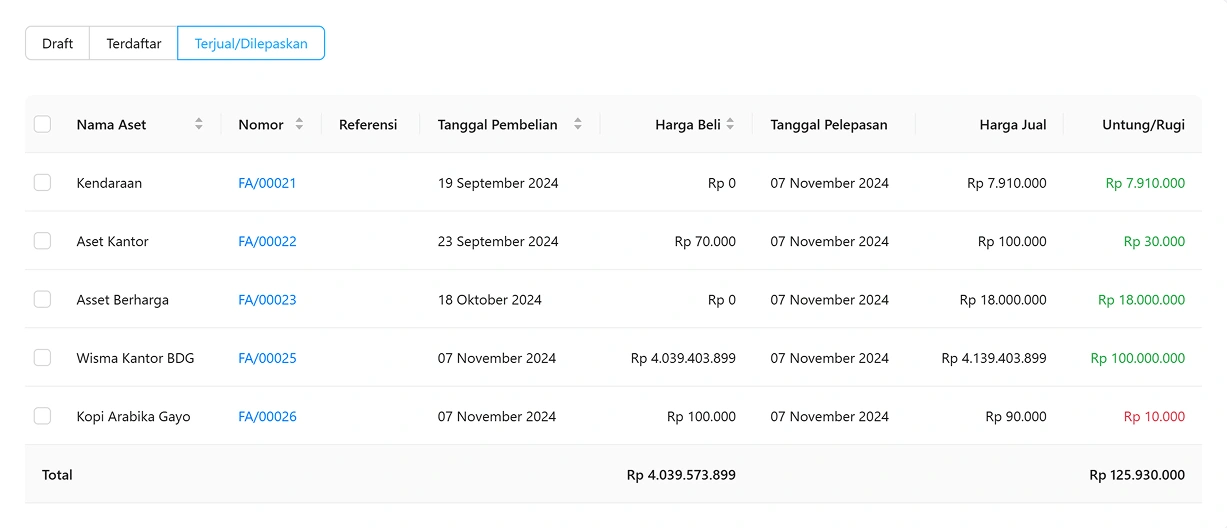
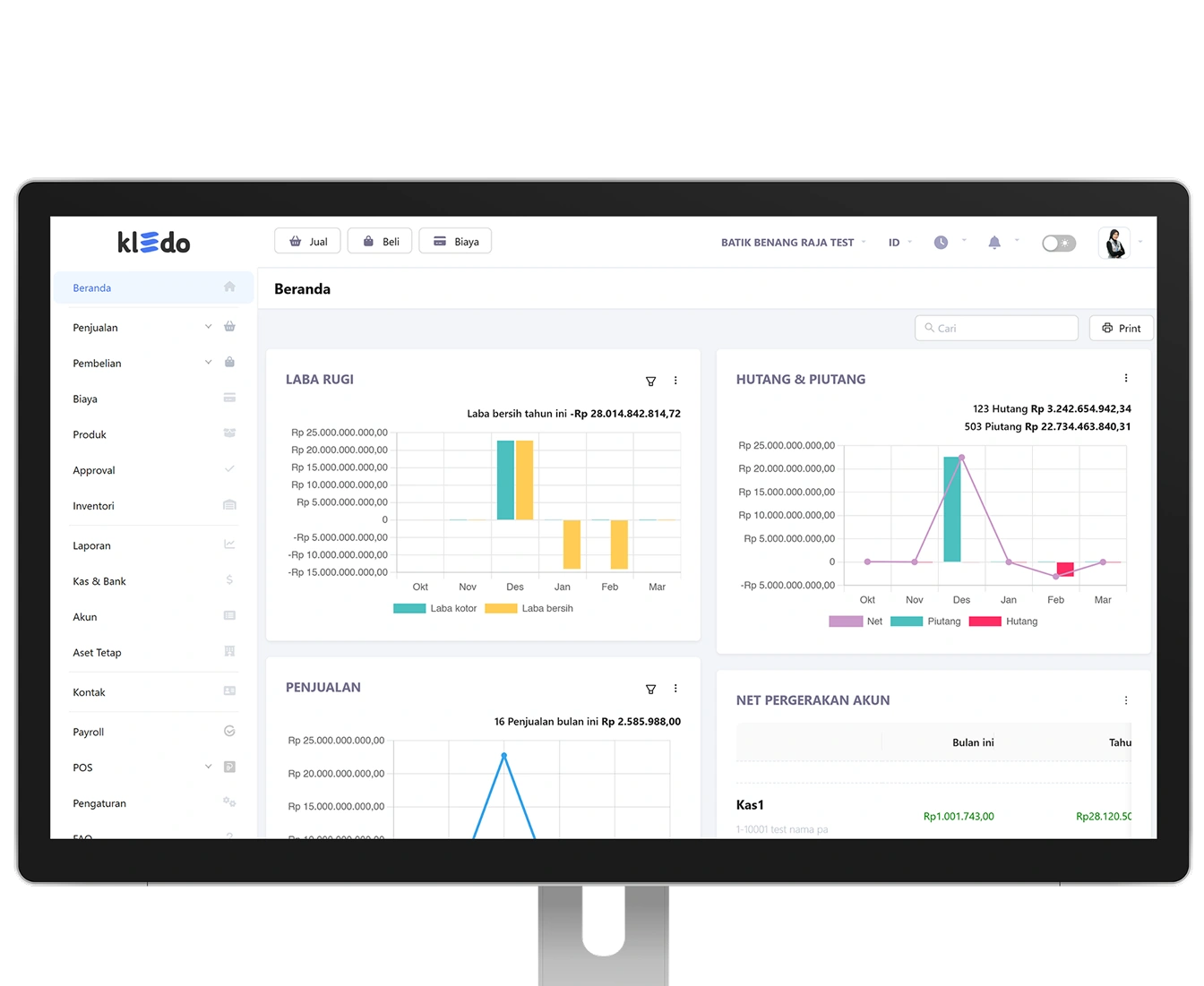
50+ Financial Reports
Make informed business decisions with accurate information about your business performance.
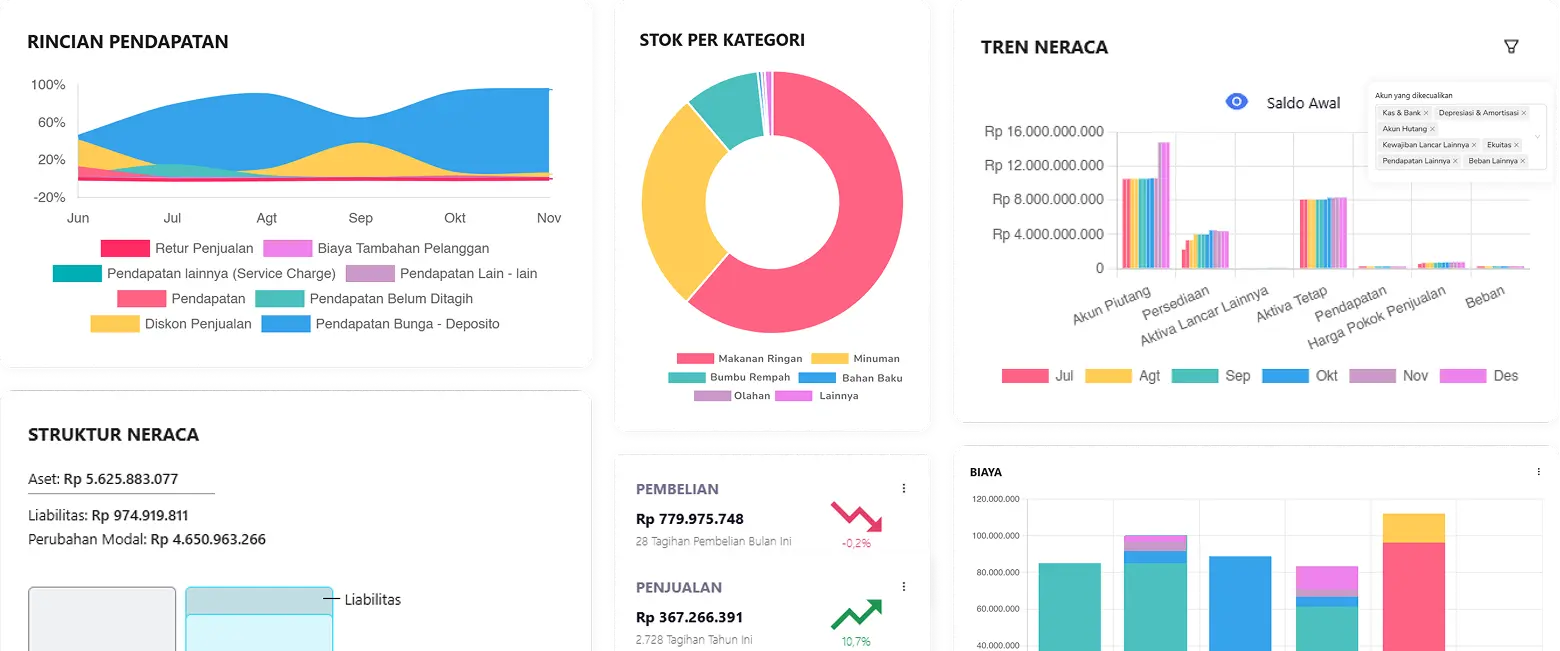
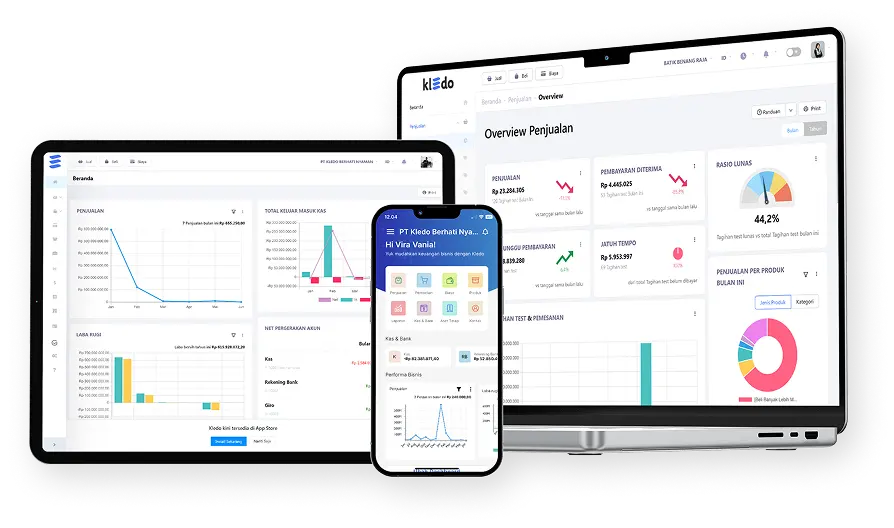
Simplify Your Business Finances
Sign up instantly and enjoy financial automation, from creating invoices, monitoring expenses, and accessing real-time reports. Fast and effective assistance makes it easy for you to focus on growing your business without the hassle of administration.
Sign up in seconds for a 14-day free trial or choose the plan that’s right for your business – hassle-free.
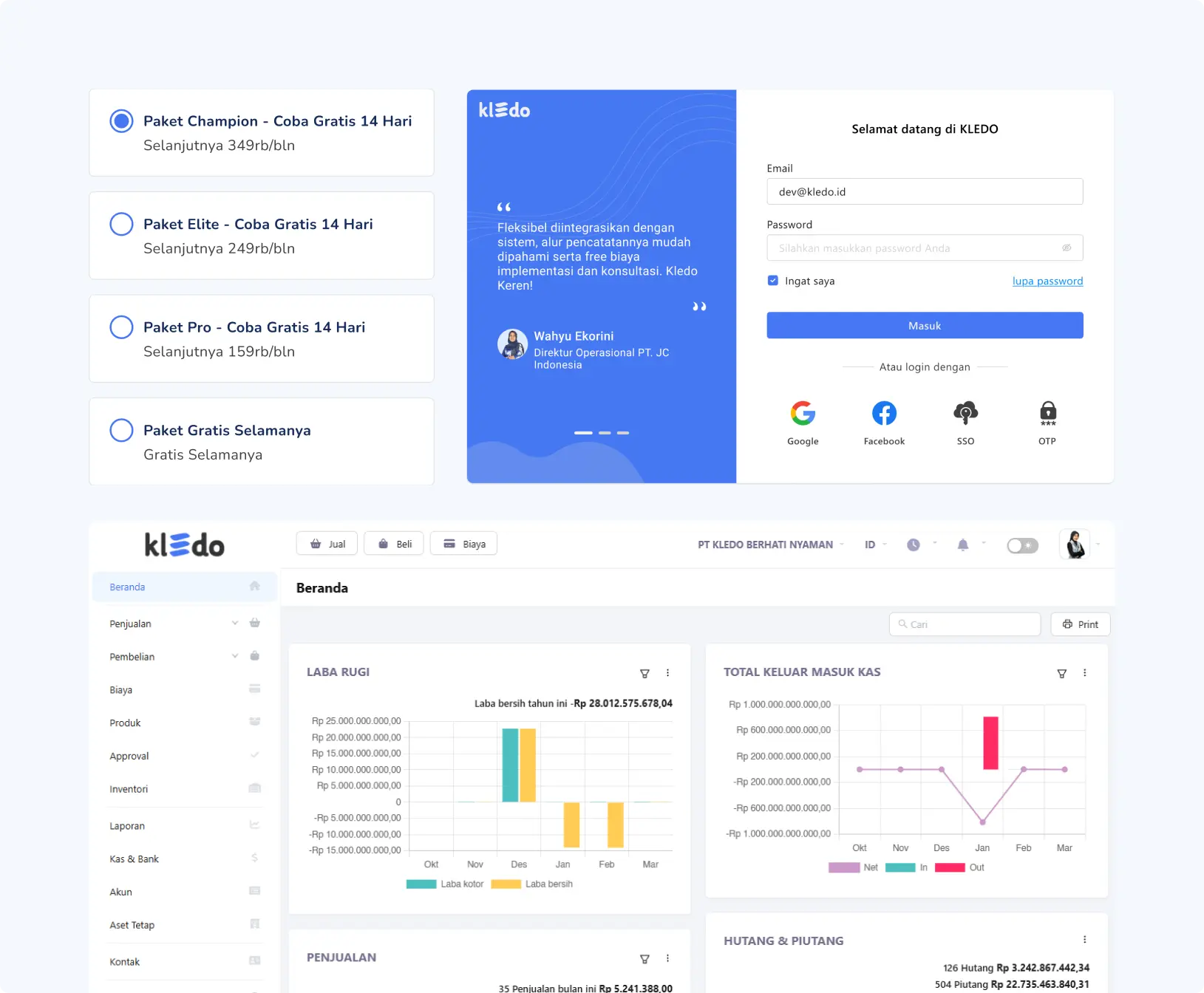
Simply log in and import transaction and financial data. Seamless integration with multiple systems means you can get to work right away.
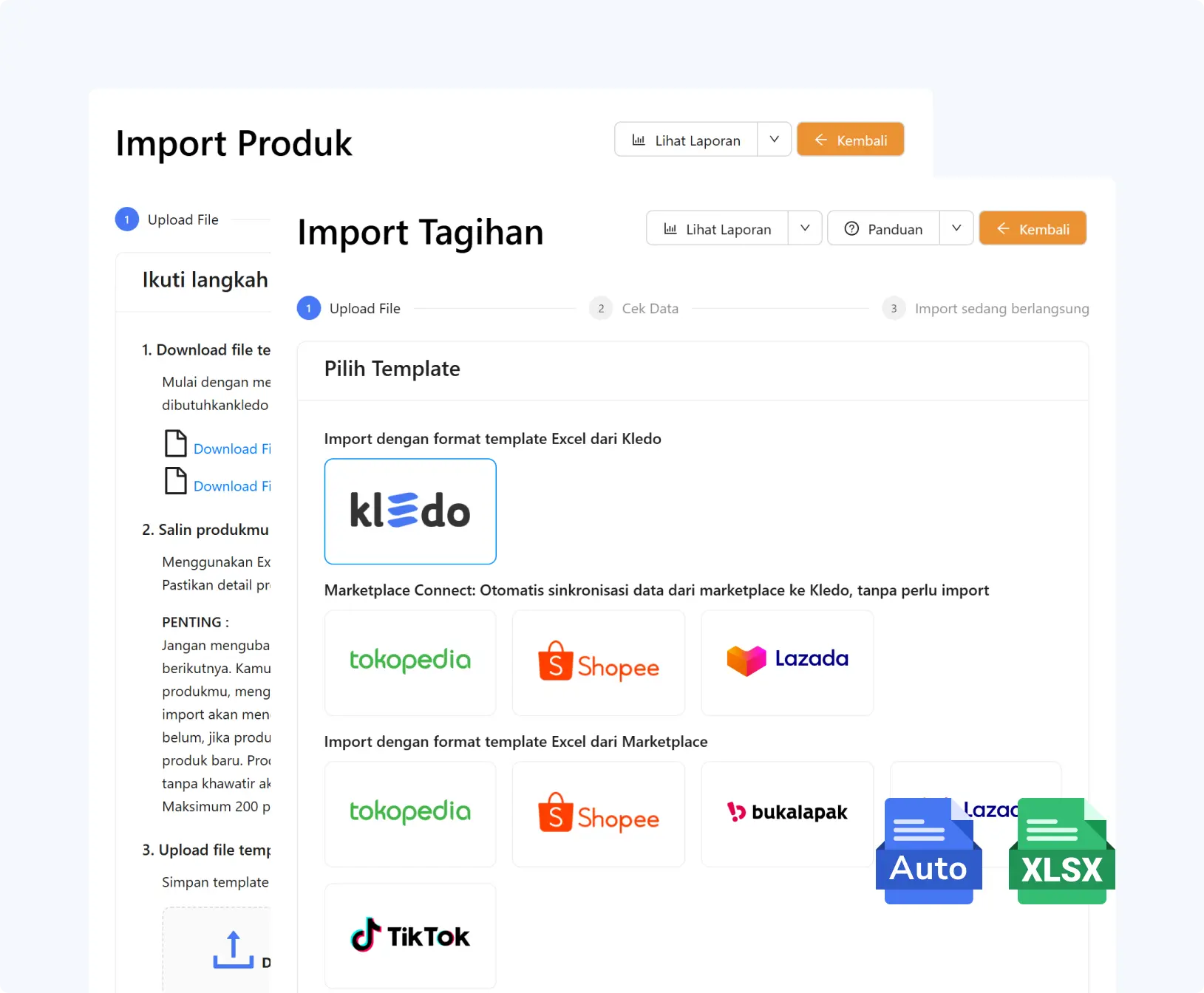
Enjoy the ease of managing your finances with our superior features:
- Instant Invoice: Create and send invoices quickly.
- Manage Expenses: Monitor purchases and expenses accurately.
- Inventory Control: Track stock and fixed assets in real-time.
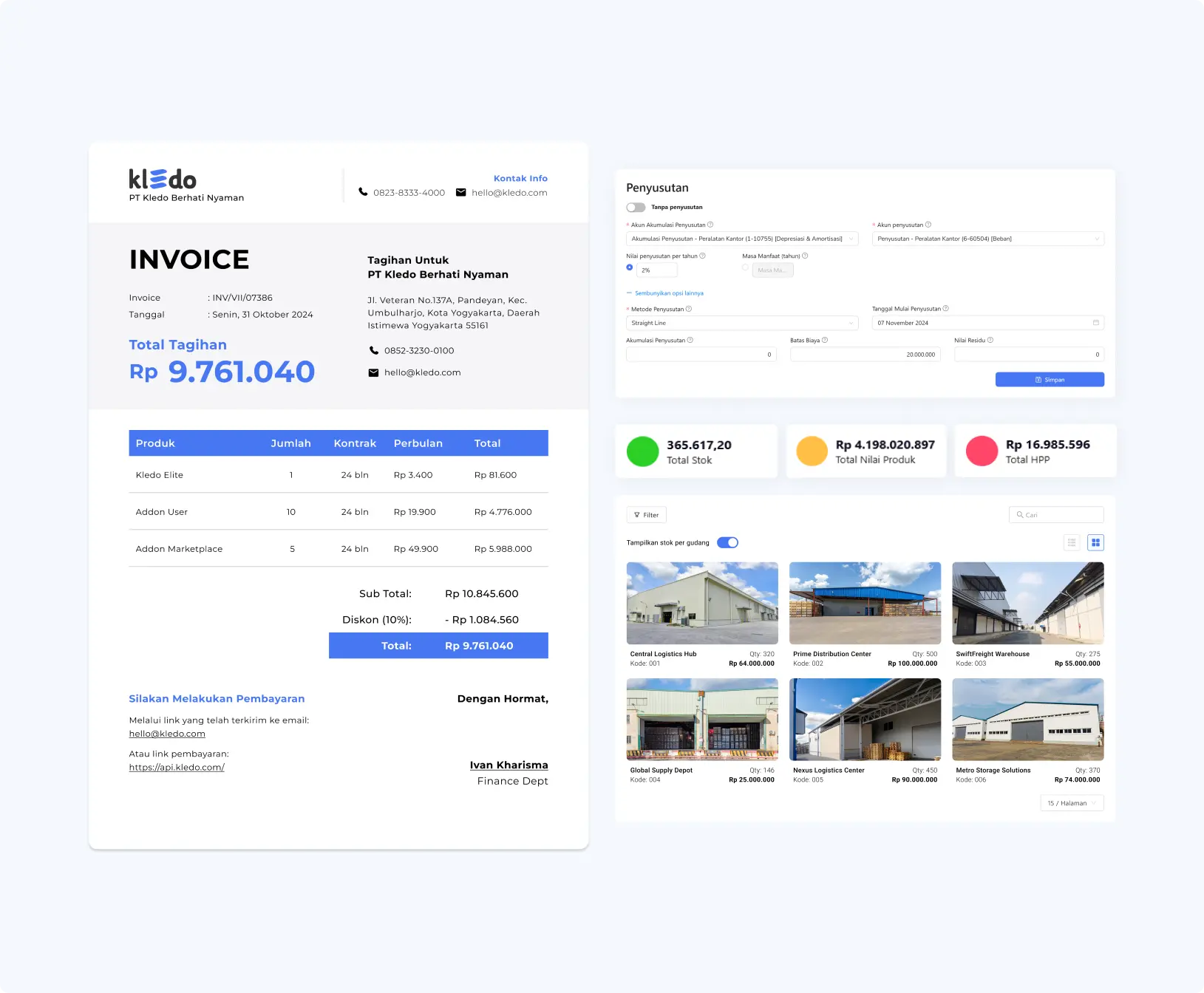
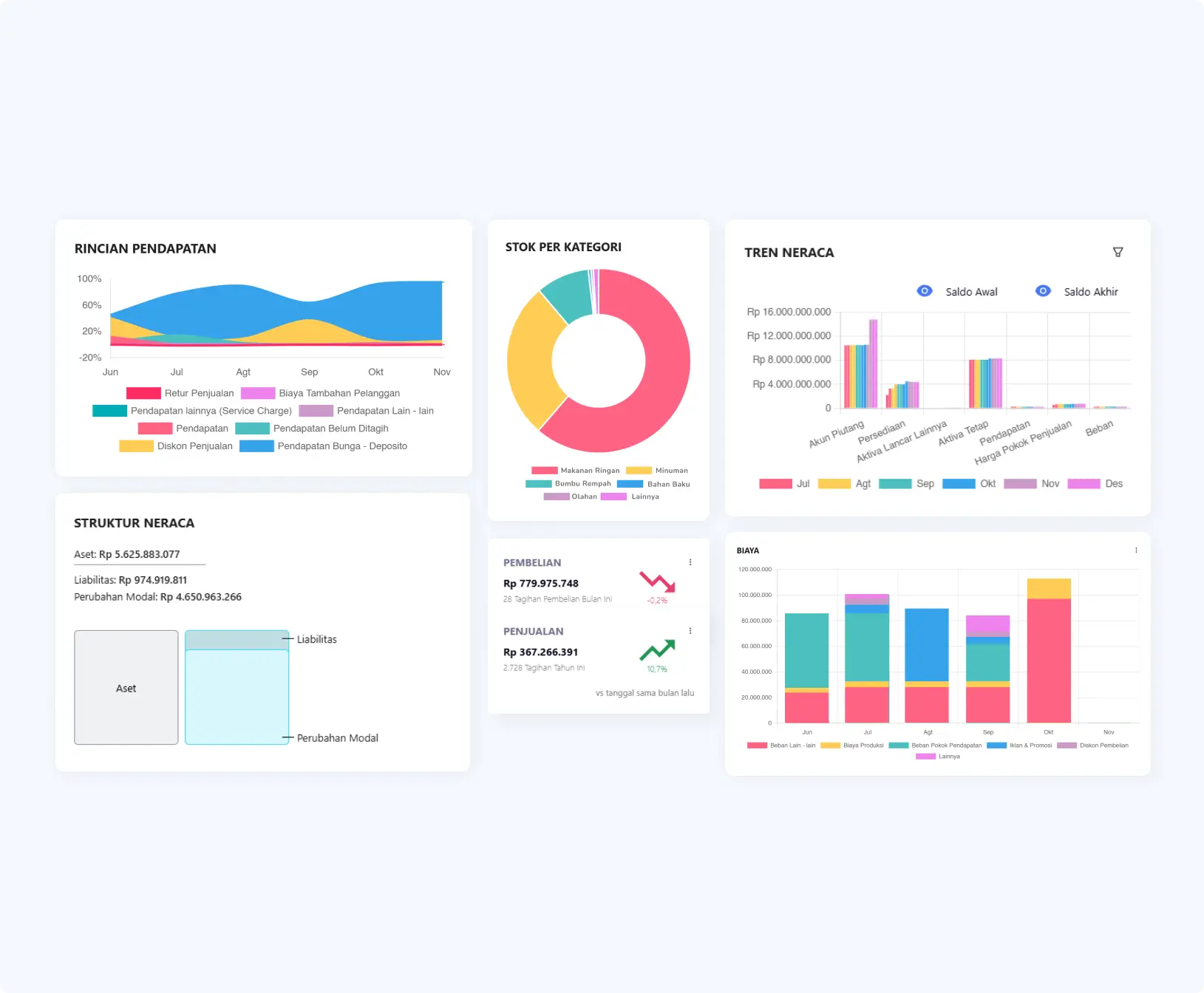
Get in-depth insights from over 50 real-time financial reports. Up-to-date data for informed business decisions.
Our support team is ready to assist you during business hours, ensuring any accounting issues are resolved quickly and effectively.
Great Features, Low Prices — No Compromises!
Save 35% with annual subscription
-
1 User
-
Expense monitoring
-
Sales & purchasing
-
Monitor cash & bank balance
-
Includes Free Plan Features
-
1 User
-
1 Warehouse
-
Complete Business Flow
-
Stock Management
-
Multi Location and Multi Project
-
Includes Pro Plan Features
-
2 Users
-
10 Warehouses
-
Manufacturing Products
-
Marketplace Connect***
-
Advanced Sales Commission
-
Custom Invoice Template ***
-
Join Invoice
-
Includes Elite Plan Features
-
5 Users
-
20 Warehouses
-
Budgeting
-
Subsidiary Consolidation
-
Multi-Currency
-
Approval
-
Proforma Invoice
****Custom invoice templates & marketplace connect are available in the Elite package and above, with optional add-on purchases.
View package comparison for full details.Words That Speak Volume
-


“For my newly-founded business, Kledo has helped a lot! It is rich in features, simple, and easy to use even for those who are not familiar with accounting.”

Ferry Wiharsato
Co Founder Kerjoo
-


“Kledo has a simple interface that helps us manage business finances effortlessly. It also comes with comprehensive features, we can record incoming order, payment, and even create invoice for customer who haven’t completed their payment.”

Pria Bagus Adi Wijaya
Niffly Jewerly
-


“Kledo Customer support’s explanation was helpful and easy to understand. Turns out using accounting software isn’t as difficult as we thought.”

Mariana Ros Afianti
Owner Batiklurik.id
Featured In
Frequently Asked Questions
Is it true that Kledo is free?
How are Kledo costs calculated?
What is needed to use Kledo?
Are there any additional costs for Kledo personal assistance?
What is accounting software?
Accounting software is a useful tool for managing and recording an organization’s daily financial transactions, including fixed asset management, expense management, revenue management, accounts receivable, accounts payable, subledger accounting, and reporting and analytics.
Comprehensive accounting software tracks an organization’s assets, liabilities, revenues, and expenses. These transactions are then automatically recorded in the general ledger in real time, giving CFOs, accountants, and controllers direct access to accurate, real-time financial data. It also allows business owners to see visibility into their performance at the operational level.
In Indonesia, there are many accounting software available, ranging from free to paid. You can choose one that suits your needs and budget.
What is the function of accounting software for business?
Accounting software automates core accounting tasks, such as journal entries, reporting, analytics, and forecasting. It simplifies accounting procedures and makes them clearer, even for nonprofessionals.
The automated system calculates the numbers for balance sheets and other financial reports. In addition, it presents the data in a sophisticated, easy-to-read format that is convenient to send and easy to read.
Accounting software such as Kledo has a number of important functions in business. This system maintains the security of financial data by introducing access rights and other security solutions.
Kledo ensures that information is available when needed in real time with standardized security cloud storage.
Kledo will provide companies with a better understanding of the company’s financial condition, help conduct analysis and forecasting, and strengthen credibility among their partners and clients.
Online or desktop accounting software, which is better?
The answer to this really depends on your needs & size of business. If you are a convenience store owner, start-up or other small business owner, then you can start with online accounting software, as it does not require installation costs or special hardware specifications. You can have a software subscription and start it at a low price or even free like in Kledo.
On the other hand, organizations sometimes need to deal with huge data. For the sake of security & ease of data management, they prefer to use desktop software. Although online accounting software is equally secure but still sometimes offline software is the solution they take. Also, to manage storage space & data, they can shift some of the data to cloud servers, The rest can remain on on-premise servers.
Desktop software is great if you work in a location that often experiences network problems. While online accounting software is perfect for those of you who often work remotely, and require seamless integration with other business operational software.
So, depending on your needs and preferences, you can choose either of the two types of accounting software. However, if you want better flexibility and security, then online accounting software might be a better choice.
Is there any free accounting software?
Currently there are various choices free accounting software in Indonesia that you can choose, one of which is Kledo accounting software which has the most complete features and is very easy to use both via PC and laptop.
You can even use Kledo via smartphone which can be downloaded at Playstore or Appstore.
What are the recommended accounting software in Indonesia?
There are many types and brands of retail business accounting software available on the market, ranging from desktop or cloud accounting software. Free to paid.
Some of the best types of accounting software include Quickbooks, Xero, FreshBooks, Zoho Books, Sage 50cloud, Kledo.
The type of accounting software that is best for you depends on your needs and preferences. You can compare the features and prices of several accounting software available to find the one that best suits your needs.
How to choose the best accounting software?
To choose the best accounting software, you first need to determine your needs and preferences for accounting software. This can be the features needed, price, ease of use, customer support, etc.
Also make sure you know the unique needs of your business, you can compare the features and prices of several accounting software available. You can also read reviews and look for information about the reputation and customer support of each accounting software.
Once you have found some accounting software that suits your needs and preferences, you can try using a demo or free version of the software to see how easy it is for you to use and how good the features it offers.
If you feel confident with the accounting software you choose, you can buy and use it to manage your company’s finances. Don’t forget to continue to monitor and evaluate the performance of the accounting software to ensure that it meets all your business needs.
What are the mandatory features that must be present in accounting software?
- Financial transaction recording: This feature makes it easy for you to record all financial transactions that occur in your company, such as purchases, sales, payments, etc.
- Financial report generation: This is a must-have feature, and it allows you to create financial reports such as balance sheet, profit and loss report, and cash flow report. These financial reports are very important to know your company’s financial position.
- Integration with third-party software: Integration is essential for today’s business processes. With the integration feature of your accounting software with third-party software such as HRIS systems, POS systems, and other platforms, it will help you manage your company as a whole more efficiently and practically.
- Customer support: No one wants to deal with a service provider who is difficult to reach. Make sure you get the best customer support if you want to make it easier for you to get troubleshooting when you have difficulties, questions, or issues related to using the software. This is very important to ensure that you can use the accounting software smoothly.
Is it safe to use Kledo?
Kledo takes serious responsibility for the security obtained by customers. In addition, the excellence of software, systems, and data is our top priority.
Security is also key to our offerings. Therefore, all information you provide is encrypted and protected with leading technology and security.
Kledo has been standardized ISO/IEC 27001. ISO/IEC 27001 itself is an international standard that sets specifications for an information security management system or Information Security Management System (ISMS).
To find out more about security standards at Kledo, you can read about it via this link
Got questions? Reach out to us on WhatsApp:
+62 852 3230 0100